Cyber Security and Ethical Hacking
By completing this course, learners will be able to:Explain core cybersecurity, hacking, and ethical hacking concepts.Set up a virtualized hacking lab with Kali Linux and supporting tools.Use Linux commands and understand Linux file structures for security testing.Understand IP addressing, MAC addressing, network devices, and the OSI/TCP models.Perform reconnaissance and footprinting using open-source intelligence (OSINT) tools.Conduct network scanning, vulnerability assessment, and exploitation of vulnerable machines.Exploit Linux, Windows, and Android systems using various attack vectors.Create simple malware and remote sessions for educational purposes.Use Google Dorks, Shodan, and VirusTotal for information gathering.Perform privilege escalation on vulnerable systems.Conduct phishing simulations and understand social engineering tactics.Use Burp Suite to analyze and exploit web application vulnerabilities.Exploit web applications via SQL Injection, XSS, and data tampering.Capture and analyze network traffic with Wireshark.Hijack sessions and steal cookies in a controlled lab.Crack Wi-Fi passwords and test wireless security.Perform exploit development and reverse engineering on simple binaries.Conduct memory and disk forensics, analyze logs, and report incidents.Solve CTF-style challenges and build a cybersecurity portfolio.Follow responsible disclosure guidelines and practice ethical hacking legally.
Blogs for Cyber Security and Ethical Hacking, Topic ZeebSploit - Information Gathering, Scanning & Exploitation Tool
Zeebsploit is a web application penetration testing tool used for information gathering, scanning, and exploiting vulnerabilities. Zeebsploit can perform the following information gathering tasks.
- Content Management Information (CMS) identification
- Port scanning
- Header information
- IP geolocation
- Email finding
- Traceroute information
- WHOIS record
- txt record
Zeebsploit can find the following web related vulnerabilities.
- Sub-domains
- Sub-domain takeover vulnerabilities
- SQLi vulnerabilities
- Cross Site Scripting (XSS)
- Directory scanning
- Admin pages
- Local File Inclusion (LFI) vulnerabilities
Similarly, Zeebsploit can take over WordPress, Joomla, and Drupal CMS through following exploits.
- WordPress content injection (currently exploits only version 4.7 and 4.7.1)
- WordPress file upload through Revsilder, Learndash, and Showbiz plugins
- Joomla file upload
- Joomla auto shell upload
- Joomla auto get config through component manager
- Drupal remote command execution
Zeebsploit Installation
To install Zeebsploit, clone the tool using the following command.
git clone https://github.com/jaxBCD/Zeebsploit.git
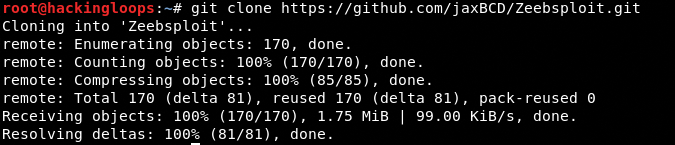
Navigate to the tool’s directory and complete the installation process by following these commands.
cd Zeebsploit
chmod +x install
./install
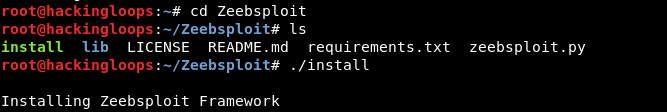
The above commands automatically install all the packages required by Zeebsploit.
How Zeebsploit Works
Zeebsploit can be set into action by running the following command.
python3 zeebsploit.py
The tool has built-in modules to perform the aforementioned tasks. These modules are divided into three categories that can be seen by typing help in the command line.
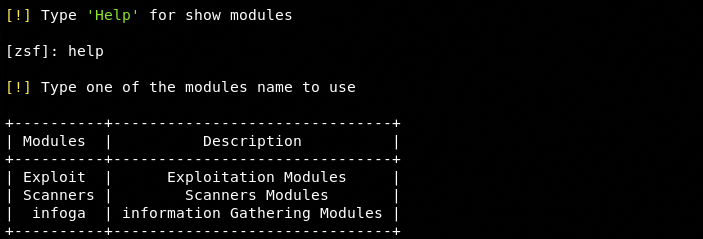
Information Gathering Modules
The information gathering modules can be set into action by typing the following command.
infoga
The help command shows all the modules available in this category.
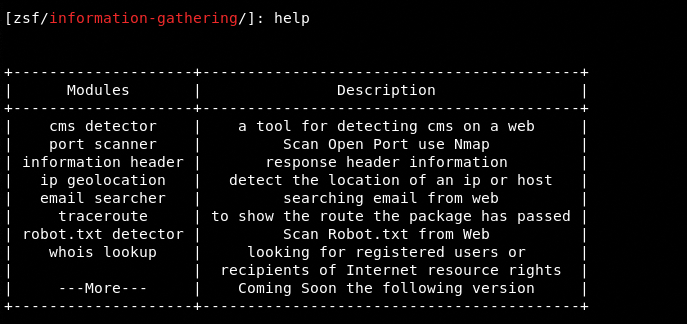
The available modules can be selected by typing their names in the command line. For example, we can select the port scanner module by typing the same in the command line.
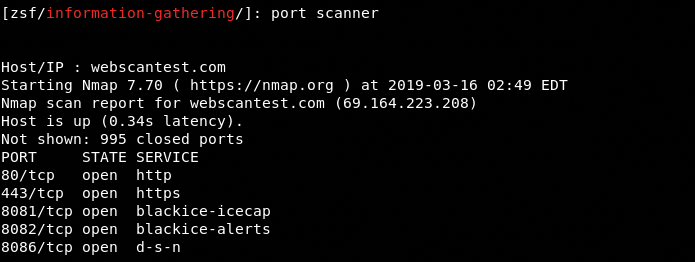
port scanner
The tool asks for the host /IP address to start scanning the target. The ports information gathered by the module can be seen in the following screenshot. The tool scans the open TCP ports and shows the running services.
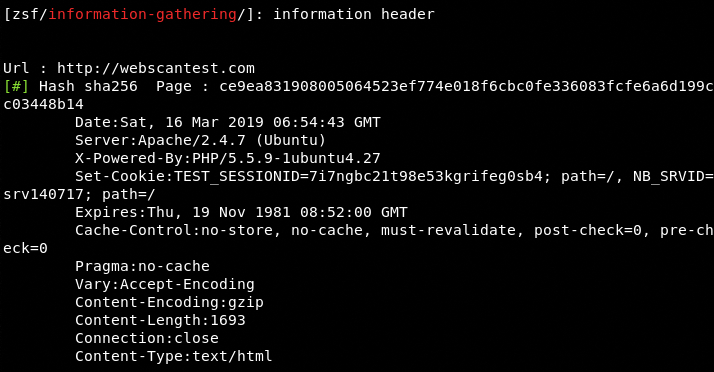
Similarly, we can get the header information by using the information header module. The header information gathered by the tool can be seen in the following screenshot.
Scanner Modules
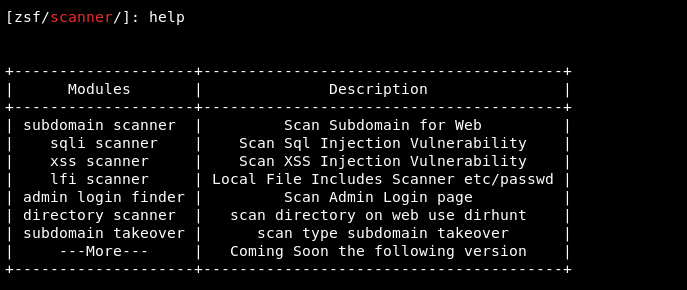
The following command loads Zeebsploit in scanner mode. The help command shows all the modules that can be used to scan the vulnerabilities mentioned in the description section of the following screenshot.
scanner
The process of using the scanner modules is similar to the information gathering modules. Type the desired module name and target host url or IP address to run the scanner. For example, we can run the cross site scripting module in the following way.
xss scanner
Once the target host/IP is provided, the tool scans all the links associated with the target host to find out the xss vulnerabilities.
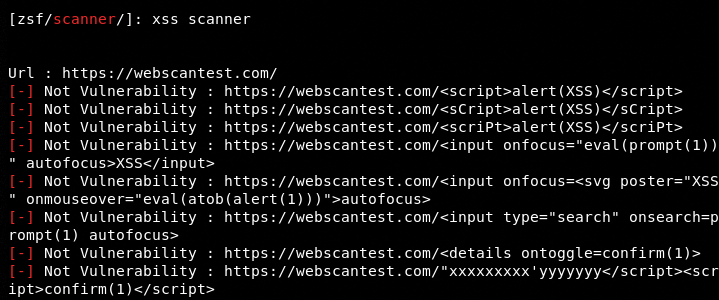
The following screenshot shows the vulnerable links found on a test host by the tool.
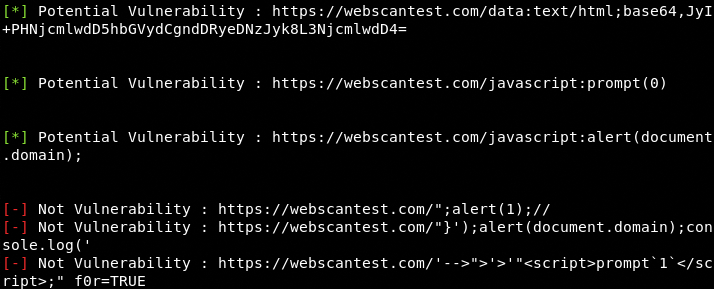
Exploit Modules
The following command is used for the exploit modules.
exploit
The available exploit modules can be seen by typing the help command.
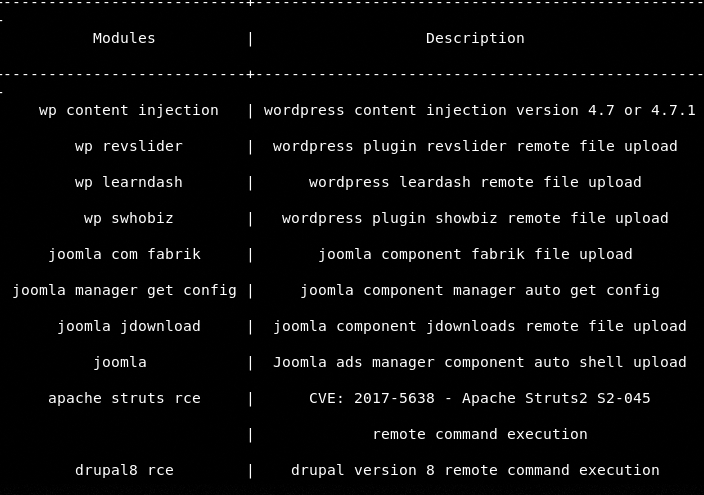
The process of running the exploit modules is similar to the information gathering and scanning modules.
Conclusion
Zeebsploit is a decent penetration testing tool that can perform most of the tasks required by red teamers. The current scope of scanning and exploitation is limited as the tool does not support all the major vulnerabilities. The tool can become very handy with the addition of more scanning and exploitation modules.
Hide Comments
Blogs for Cyber Security and Ethical Hacking, Topic Recon-ng v5
What is recon-ng?
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience.
Running recon-ng from the command line you enter a shell like environment where you can configure options, perform recon and output results to different report types.
The interactive console provides a number of helpful features such as command completion and contextual help.
Recon-ng 5 comes without modules, which is also one of the major differences. Also the parameters, commands, etc. have changed a bit to the previous versions.
The command options list displays the current settings and with options set the parameters
Since version 5 no modules are available by default, we add them using the command marketplace.
But first, the module list should be updated with the command marketplace refresh.
With the command marketplace info all all modules including description can be displayed.
You can search for example “hackertarget” with the command marketplace search hackertarget.
To install the module “hackertarget” the command marketplace install recon/domains-hosts/hackertarget or marketplace install hackertarget can be used
To use a module the syntax is modules load recon/domains-hosts/hackertarget and the command info to display the options as seen below.
To change the “SOURCE” option use the command options set SOURCE for example options set SOURCE rapid7.com to display the hosts of rapid7.com.
Type run to execute the module.
Add API keys to recon-ng
It is a simple matter to add API keys to recon-ng. Shodan with a Membership account is a highly recommended option.
Allowing you to query open ports on your discovered hosts without sending any packets to the target systems.
keys add shodan_api <insert shodan api key here>
Conclusion
Recon-ng is a powerful tool that can be further explored by looking through the list of modules. The help within the console is very clear and with a bit of playing around it won’t take long to become an expert.
Once you start to become more familiar with the layout of the tool you will discover options such as workspaces that allow you to segment based on organization or network.

Login to comment